2 Hacker Way
Pete Tong, John Monkman - AURORA (CHAIM Remix) [Beesemyer , CHAIM is somebody who is doing some proper remixes & I just can't hold this one back from you. This remix for Legend Pete Tong & John Monkman is pretty freak
Sales Hacker - B2B Sales Tips, Strategies, Training , Sales Hacker is the premier source of true Sales Enablement content sharing. Their events are shifting the way that knowledge is transfered by bringing together best-in-class thought leaders and practitioners to share proven & validated best practices via content, virtual, and live events..
Hacker ethic - Wikipedia, Hacker ethic is a term for the moral values and philosophy that are common in hacker culture.Practitioners of the hacker ethic acknowledge that sharing information and data responsibly is beneficial and helpful. Whilst the philosophy originated at the Massachusetts Institute of Technology in the 1950s–1960s, the term hacker ethic is attributed to journalist Steven Levy as described in his .
Facebook password hacker - Hack Facebook account in 2', Human beings from all over the world are increasingly searching for easy-used Facebook password hacker. But few of them are successful. The first reason may be that hacking a Facebook password is really a very difficult task..




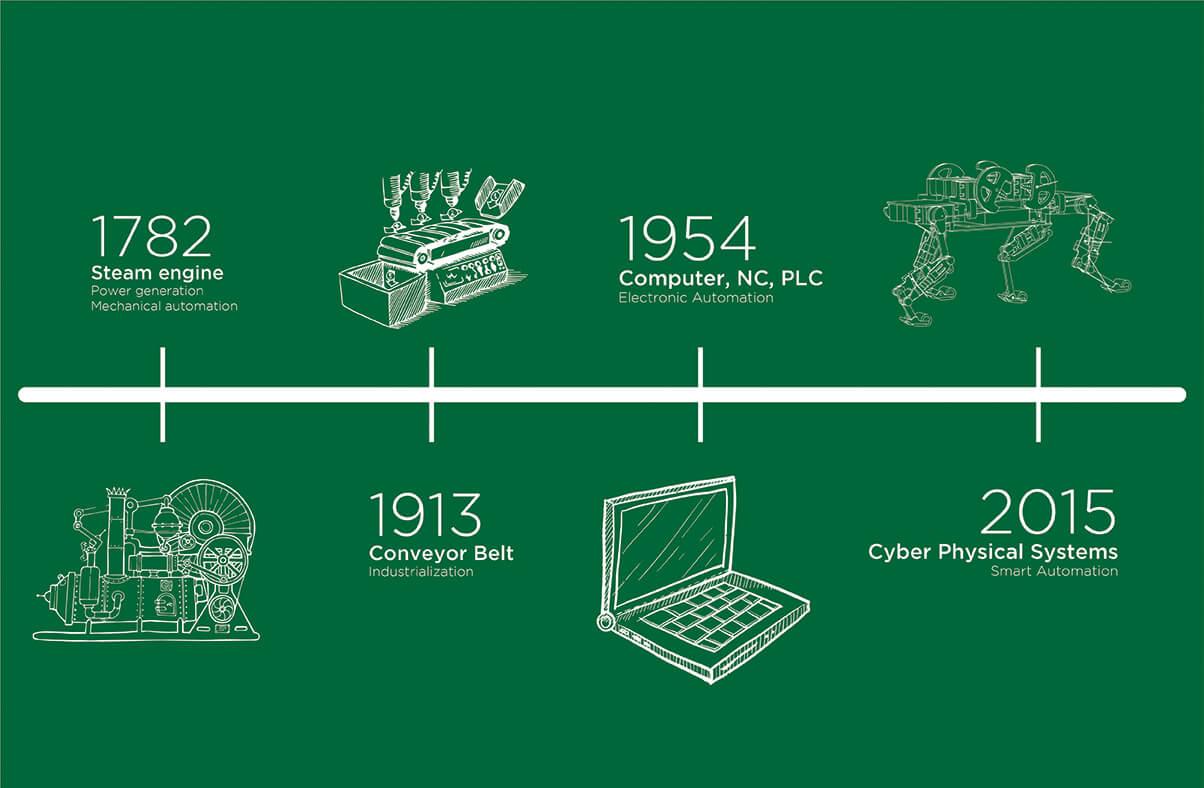


Build Better Strategies! Part 2: Model-Based Systems – The , This was the second part of the Build Better Strategies series. The third part will deal with the process to develop a model-based strategy, from inital research up to building the user interface..
Hacker culture - Wikipedia, The hacker culture is a subculture of individuals who enjoy the intellectual challenge of creatively overcoming limitations of software systems to achieve novel and clever outcomes. The act of engaging in activities (such as programming or other media) in a spirit of playfulness and exploration is termed "hacking".However, the defining characteristic of a hacker is not the activities performed .
Resource Hacker, Switch Parameter-open : filename - the name of the file that is to be modified. It should be a Windows PE file (*.exe, *.dll etc) or a compiled or uncompiled resouce file (*.res or *.rc).
The Hacker and the Ants: Version 2.0: Rudy Rucker , The Hacker and the Ants: Version 2.0 [Rudy Rucker] on Amazon.com. *FREE* shipping on qualifying offers. From a two-time winner of the Philip K. Dick award, and one of the founding fathers of cyberpunk comes a novel about a very modern nightmare: the most destructive computer virus ever has been traced to your machine. Computer programmer Jerzy Rugby spends his days blissfully hacking away in .
Hacker Typer, Ctrl+B Buy Bitcoin [Earn $10 Free]: Ctrl+L Buy AltCoins: Ctrl+P Buy More AltCoins: Ctrl+E Visual eBay Visual eBay.
Hacker Experience 2, Hacker Experience 2 is an open source real time hacking simulation. Living in a dystopic world controlled by megacorporations, you play the role of a hacker seeking money and power..

0 Response to "2 Hacker Way"
Posting Komentar